Mastering IoT Connectivity: How To Use SSH IoT From Anywhere Without Android
Whether you're a tech enthusiast, a developer, or a business professional, understanding how to use SSH IoT from anywhere without Android is a game-changer. SSH, or Secure Shell, provides a secure method to access and control IoT devices over a network, ensuring both functionality and security. This article delves into the intricacies of setting up and using SSH for IoT management, offering you a comprehensive guide to mastering this essential skill. With the right tools and knowledge, you can manage your IoT devices from anywhere in the world, even without relying on an Android device. The demand for remote IoT management has surged as smart devices become integral to both personal and professional environments. Imagine controlling your smart home appliances, monitoring industrial sensors, or troubleshooting network devices from the comfort of your laptop or desktop. SSH allows you to do just that by providing encrypted communication between your device and the IoT hardware. This ensures that your data remains secure while you execute commands, transfer files, or configure settings. By exploring how to use SSH IoT from anywhere without Android, you’ll gain the flexibility to manage your IoT ecosystem without being tied to a specific operating system or device. This guide is designed to equip you with actionable insights, step-by-step instructions, and expert tips to seamlessly integrate SSH into your IoT workflow. From setting up SSH on your devices to troubleshooting common issues, we’ll cover all aspects of remote IoT management. Whether you’re a beginner or an experienced user, this article will help you harness the full potential of SSH for IoT. By the end, you’ll not only understand how to use SSH IoT from anywhere without Android but also appreciate the broader implications of secure remote access in the IoT landscape.
Table of Contents
- What is SSH and Why is it Important for IoT?
- How Can You Set Up SSH for IoT Devices?
- Is It Possible to Use SSH IoT from Anywhere Without Android?
- Tools and Software to Enhance Your SSH IoT Experience
- What Are the Common Challenges When Using SSH for IoT?
- How to Troubleshoot SSH IoT Connection Problems?
- Best Practices for Secure and Efficient SSH IoT Management
- Frequently Asked Questions About SSH IoT
What is SSH and Why is it Important for IoT?
SSH, or Secure Shell, is a cryptographic network protocol that allows secure communication between two devices over an unsecured network. It is widely used for remote command execution, file transfers, and device management. In the context of IoT, SSH plays a pivotal role in ensuring secure and reliable access to devices. By encrypting data during transmission, SSH prevents unauthorized access and eavesdropping, making it an indispensable tool for managing IoT ecosystems.
One of the primary reasons SSH is crucial for IoT is its ability to provide a secure channel for remote administration. IoT devices often operate in environments where physical access is limited or impractical. For instance, a smart thermostat installed in a remote location or a sensor deployed in an industrial plant may require periodic updates or troubleshooting. SSH enables administrators to connect to these devices securely, execute commands, and retrieve logs without needing to be physically present.
Read also:How To Access Remoteiot Behind Router Raspberry Pi Free Download A Comprehensive Guide
Moreover, SSH supports various authentication methods, including password-based and key-based authentication. Key-based authentication, in particular, is highly recommended for IoT devices as it eliminates the risk of brute-force attacks. By generating a pair of cryptographic keys—one private and one public—users can authenticate themselves without transmitting passwords over the network. This enhances security and ensures that only authorized individuals can access the IoT devices. In summary, SSH is not just a tool but a cornerstone of secure IoT management.
How Can You Set Up SSH for IoT Devices?
Setting up SSH for IoT devices involves a series of steps to ensure seamless and secure connectivity. The process begins with enabling SSH on the IoT device itself, followed by configuring the network and choosing an appropriate SSH client. By following these steps, you can establish a robust connection that allows you to manage your IoT devices remotely.
Choosing the Right SSH Client
Selecting the right SSH client is critical for a smooth experience. Popular SSH clients include PuTTY for Windows, OpenSSH for Linux and macOS, and Termius for cross-platform use. Each client has its own set of features and compatibility options. For example, PuTTY is lightweight and easy to use, making it ideal for beginners, while OpenSSH offers advanced customization for experienced users.
Configuring Your IoT Device for SSH
Once you’ve chosen an SSH client, the next step is to configure your IoT device for SSH access. This typically involves enabling the SSH service on the device and setting up authentication credentials. For devices running Linux-based operating systems, you can enable SSH by installing the OpenSSH server package and configuring the SSH daemon. On the other hand, devices with proprietary firmware may require specific steps outlined in the manufacturer’s documentation.
After enabling SSH, it’s essential to secure your connection by setting up key-based authentication. Generate a public-private key pair on your computer and copy the public key to the IoT device. This ensures that only devices with the corresponding private key can access the IoT device, significantly enhancing security. Additionally, consider changing the default SSH port and disabling password authentication to further protect your device from unauthorized access.
Is It Possible to Use SSH IoT from Anywhere Without Android?
Absolutely! Using SSH IoT from anywhere without Android is not only possible but also straightforward with the right setup. The key lies in leveraging tools and techniques that allow you to bypass the limitations of mobile operating systems and access your IoT devices from any device with internet connectivity. Whether you’re using a Windows PC, a Mac, or even a Linux machine, you can establish a secure SSH connection to your IoT devices.
Read also:How To Access Your Raspberry Pi Remotely For Free A Complete Guide
One of the most effective methods is to use a cloud-based SSH service or a remote desktop application. These services act as intermediaries, allowing you to connect to your IoT devices via a web browser or a desktop application. For instance, services like AWS IoT Core or Azure IoT Hub provide built-in SSH capabilities, enabling you to manage your devices remotely without needing to install additional software. Similarly, remote desktop applications like TeamViewer or AnyDesk can be configured to forward SSH connections, giving you access to your IoT devices from anywhere in the world.
Another approach is to set up port forwarding on your router to allow external SSH connections. By configuring your router to forward incoming SSH traffic to your IoT device, you can connect to it using its public IP address. However, this method requires careful attention to security, as exposing your IoT device to the internet increases the risk of unauthorized access. To mitigate this risk, consider using a Virtual Private Network (VPN) to encrypt your connection and restrict access to trusted IP addresses. With these strategies in place, you can confidently use SSH IoT from anywhere without Android.
Tools and Software to Enhance Your SSH IoT Experience
To maximize the efficiency and security of your SSH IoT setup, it’s essential to leverage the right tools and software. These tools not only simplify the process of connecting to your IoT devices but also enhance the overall user experience by providing additional features and functionalities.
One of the most popular tools for SSH IoT management is **Termius**. Available on multiple platforms, including Windows, macOS, and Linux, Termius offers a user-friendly interface and supports key-based authentication. Its cross-platform synchronization feature allows you to access your SSH configurations and session history from any device, making it an excellent choice for users who frequently switch between devices.
For those looking for a more advanced solution, **MobaXterm** is a powerful SSH client that combines a terminal emulator, file transfer tool, and network utilities into a single application. It supports multi-tabbed sessions, scripting, and even graphical desktop sharing, making it ideal for managing complex IoT ecosystems. Additionally, **WinSCP** is another valuable tool for secure file transfers between your computer and IoT devices. It integrates seamlessly with SSH and supports drag-and-drop functionality, simplifying the process of uploading or downloading files.
What Are the Common Challenges When Using SSH for IoT?
While SSH is a powerful tool for IoT management, it is not without its challenges. Understanding these challenges and knowing how to address them is crucial for maintaining a secure and efficient IoT ecosystem.
Network Configuration Issues
One of the most common challenges users face is configuring their network to allow SSH access. Firewalls, NAT (Network Address Translation), and ISP restrictions can all interfere with SSH connections. For instance, if your IoT device is behind a NAT, you may need to configure port forwarding on your router to ensure that SSH traffic reaches the device. Similarly, some ISPs block certain ports by default, requiring you to use non-standard ports for SSH.
Security Concerns and How to Address Them
Security is another significant concern when using SSH for IoT. Exposing your IoT devices to the internet increases the risk of unauthorized access, especially if weak passwords or outdated firmware are used. To mitigate these risks, always use key-based authentication instead of passwords and keep your IoT device’s firmware up to date. Additionally, consider implementing a firewall or intrusion detection system to monitor and block suspicious activity.
How to Troubleshoot SSH IoT Connection Problems?
Troubleshooting SSH IoT connection issues requires a systematic approach to identify and resolve the root cause. Common problems include incorrect IP addresses, blocked ports, and misconfigured SSH settings. Start by verifying that the IoT device is powered on and connected to the network. Use tools like ping or traceroute to confirm connectivity and check for any network bottlenecks.
If the issue persists, review your SSH configuration files for errors. Ensure that the SSH service is running on the IoT device and that the correct port is being used. For devices behind a NAT, double-check your port forwarding settings and ensure that the external IP address is correctly mapped to the internal IP address of the IoT device. Finally, consult the logs on both the client and server sides to identify any error messages or warnings that may provide additional clues.
Best Practices for Secure and Efficient SSH IoT Management
To ensure secure and efficient SSH IoT management, follow these best practices:
- Use key-based authentication instead of passwords.
- Change the default SSH port to reduce the risk of brute-force attacks.
- Regularly update your IoT device’s firmware and SSH software.
- Monitor your SSH logs for suspicious activity and take immediate action if necessary.
Frequently Asked Questions About SSH IoT
What is the difference between SSH and Telnet?
SSH and Telnet are both protocols for remote device management, but SSH is more secure as it encrypts data during transmission, while Telnet sends data in plain text.
Can I use SSH on IoT devices without internet access?
Yes, SSH can be used on local networks without internet access, provided both the client and IoT device are connected to the same network.
How do I generate SSH keys for IoT devices?
You can generate SSH keys using tools like ssh-keygen on Linux or PuTTYgen on Windows. Simply follow the prompts to create a public-private key pair and copy the public key to the IoT device.
In conclusion, mastering how to use SSH IoT from anywhere without Android opens up a world of possibilities for
Top Tips For Accessing The Best IoT Device SSH On Android
Understanding NSFW Twitter: A Comprehensive Guide To Its Impact And Usage
How To Master Raspberry Pi Remote Access Control For Free

IoT Anywhere Archives Beecham Research
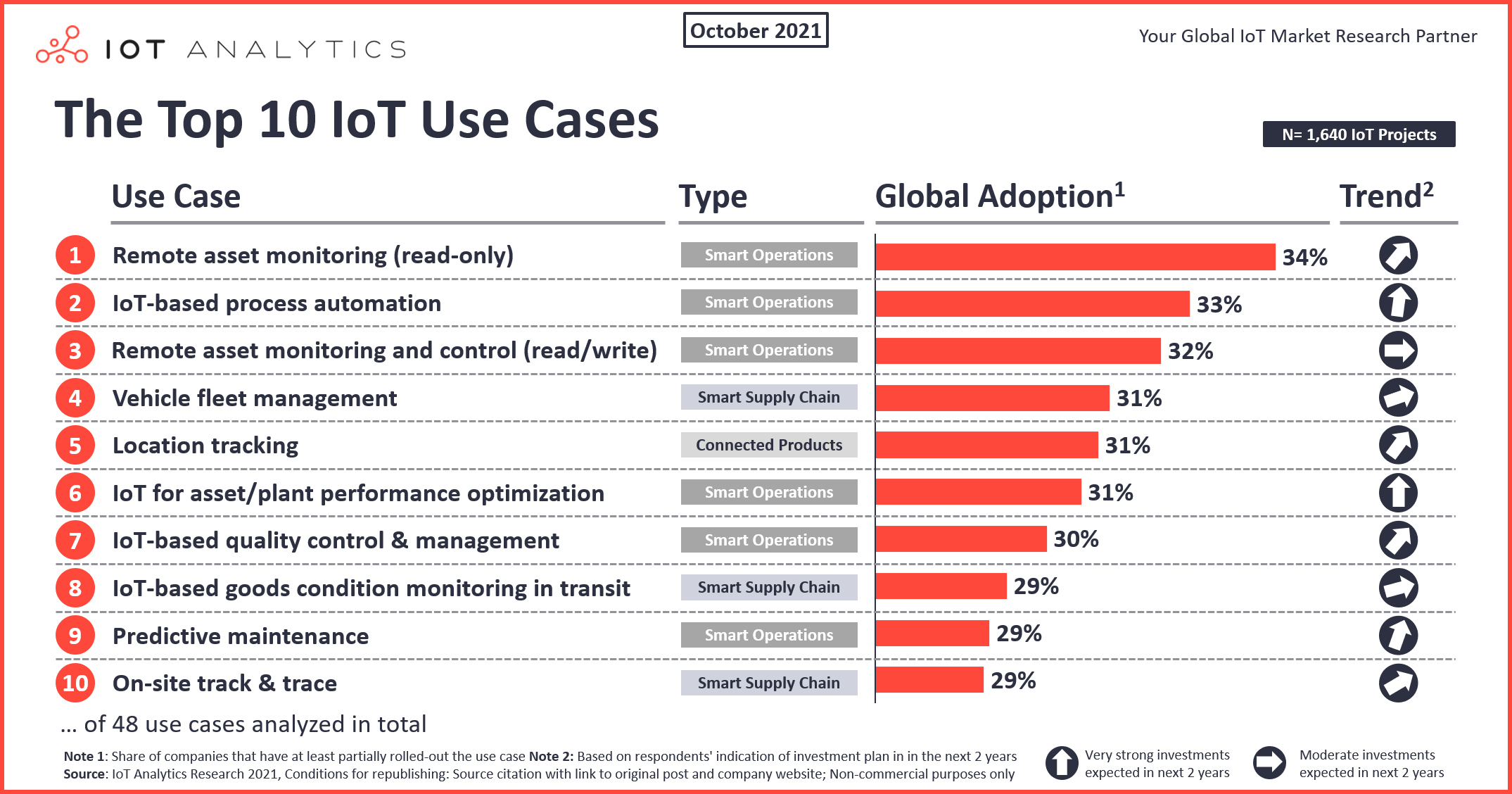
IoT Top 10 IoT use cases—and what they demand from your network TACS