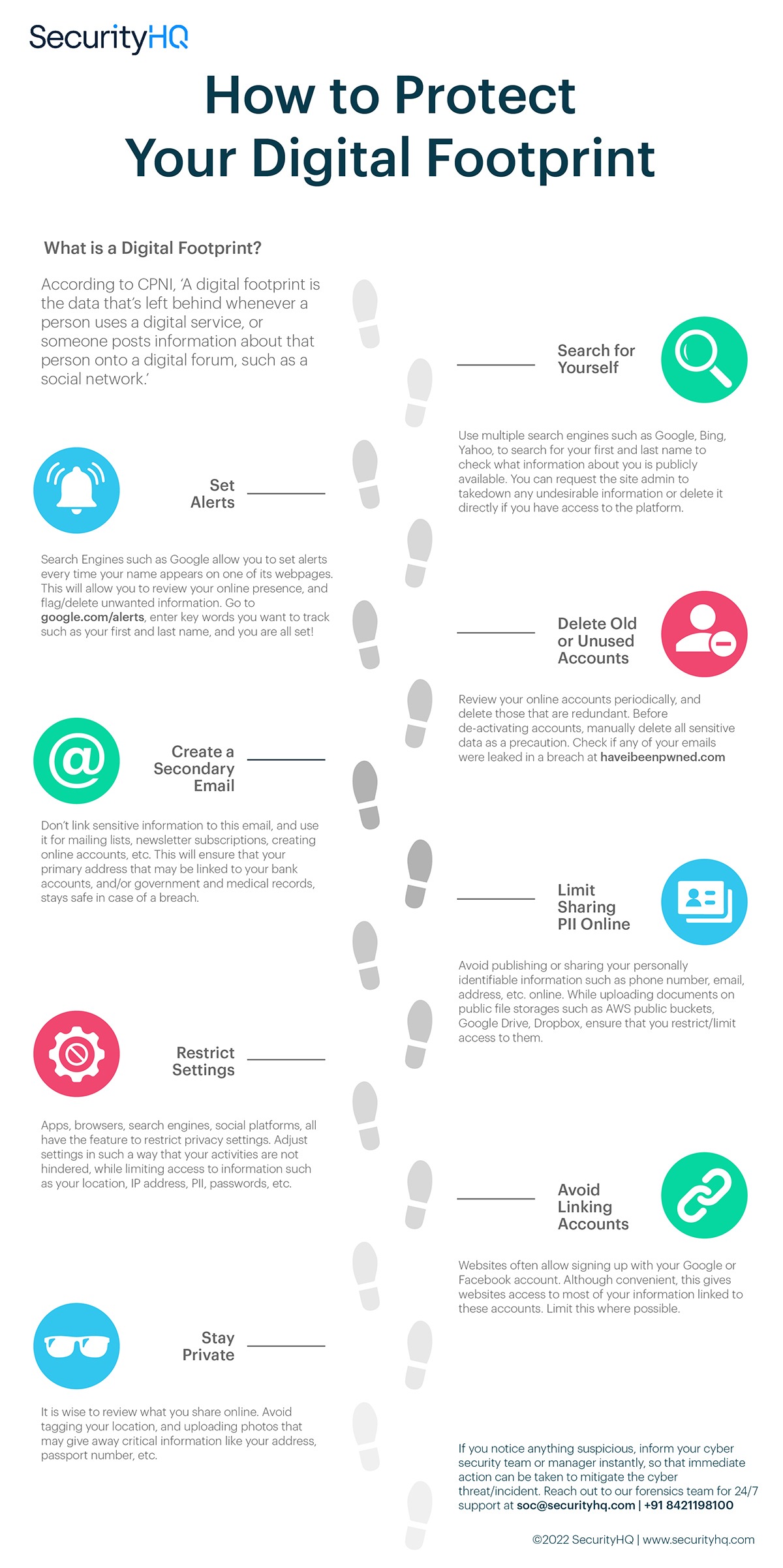
Understanding IP Footprints: A Comprehensive Guide
Have you ever wondered how your online activities leave behind digital traces that can be tracked and analyzed? These traces, known as IP footprints, are an essential aspect of your online presence. Every time you access the internet, your device communicates with servers, websites, and other devices, leaving behind a unique identifier known as an IP address. This address not only facilitates communication but also serves as a marker of your digital activity. Understanding IP footprints is crucial for safeguarding your privacy and ensuring secure online interactions.
In today's digital age, where data breaches and cyber threats are increasingly common, being aware of your IP footprint is more important than ever. Whether you're an individual browsing the web or a business managing sensitive customer data, knowing how IP footprints work can help you mitigate risks and protect your information. From tracking online behavior to identifying potential vulnerabilities, IP footprints play a significant role in shaping your digital experience.
This article will delve into the intricacies of IP footprints, explaining what they are, how they are created, and why they matter. We'll explore their implications for privacy and security, as well as strategies to minimize your digital footprint. By the end of this guide, you'll have a comprehensive understanding of IP footprints and the tools to manage them effectively.
Read also:Danielle Bregoli Net Worth A Comprehensive Look At Her Wealth And Career
Table of Contents
- What Are IP Footprints?
- How Are IP Footprints Created?
- Why Do IP Footprints Matter?
- Privacy Implications of IP Footprints
- Security Risks Associated with IP Footprints
- How to Minimize Your IP Footprint
- Tools to Track and Analyze IP Footprints
- Legal and Ethical Considerations
- Real-World Applications of IP Footprints
- Conclusion
What Are IP Footprints?
An IP footprint refers to the trail of data left behind by your device as it interacts with the internet. This trail includes your IP address, which serves as a unique identifier for your device on a network. Every time you visit a website, send an email, or stream content, your IP address is logged by the servers you interact with. These logs can reveal valuable information about your location, browsing habits, and even the type of device you're using.
IP footprints are not limited to just your IP address. They also encompass metadata such as timestamps, geolocation data, and device information. This data can be aggregated and analyzed to create a detailed profile of your online activity. While IP footprints are essential for the functioning of the internet, they also raise concerns about privacy and security.
Understanding IP footprints requires a basic knowledge of how the internet works. When you connect to the internet, your Internet Service Provider (ISP) assigns your device an IP address. This address allows other devices and servers to communicate with you. However, it also serves as a breadcrumb trail that can be followed by third parties, including advertisers, hackers, and government agencies.
How Are IP Footprints Created?
IP footprints are created every time your device communicates with the internet. Here's a breakdown of how this process works:
- Device Connection: When you connect to the internet, your ISP assigns your device an IP address. This address is necessary for identifying your device on the network.
- Server Logs: Every website or server you interact with logs your IP address. This log includes details such as the time of access, the pages visited, and the duration of your session.
- Data Aggregation: Over time, these logs can be aggregated to create a comprehensive profile of your online activity. This profile can include information about your browsing habits, preferences, and even your physical location.
The creation of IP footprints is an inherent part of using the internet. However, the extent to which your data is tracked and stored depends on the policies of the websites and services you use. Some websites may only log your IP address temporarily, while others may retain this information for extended periods.
Why Do IP Footprints Matter?
IP footprints matter for several reasons, particularly in the context of privacy and security. Here's why they are significant:
Read also:Hot Mms Everything You Need To Know About Multimedia Messaging Services
- Privacy Concerns: Your IP address can reveal sensitive information about your location and identity. This data can be used by advertisers to target you with personalized ads or by malicious actors to track your online activity.
- Security Risks: Hackers and cybercriminals can exploit IP footprints to launch targeted attacks, such as Distributed Denial of Service (DDoS) attacks or phishing scams.
- Legal Implications: In some cases, IP footprints can be used as evidence in legal proceedings. Law enforcement agencies may request access to server logs to trace the origin of illegal activities.
Understanding the significance of IP footprints can help you take proactive steps to protect your online presence. Whether you're concerned about privacy, security, or legal risks, managing your IP footprint is an essential aspect of responsible internet usage.
Privacy Implications of IP Footprints
The privacy implications of IP footprints are far-reaching. Here are some key considerations:
- Tracking and Profiling: Advertisers and data brokers use IP footprints to track your online behavior and build detailed profiles. These profiles can be used to deliver targeted ads or sold to third parties.
- Location Tracking: Your IP address can reveal your approximate location, which can be used to infer additional information about your lifestyle and habits.
- Data Retention: Some websites and services retain IP logs for extended periods, increasing the risk of unauthorized access or misuse.
To mitigate these risks, it's important to be aware of how your data is being collected and used. Reading privacy policies, adjusting browser settings, and using privacy-focused tools can help you minimize your exposure.
Security Risks Associated with IP Footprints
IP footprints can pose significant security risks, particularly if they fall into the wrong hands. Here are some common threats:
- Hacking and Exploitation: Cybercriminals can use your IP address to identify vulnerabilities in your network or launch targeted attacks.
- DDoS Attacks: Distributed Denial of Service (DDoS) attacks can overwhelm your network by flooding it with traffic from multiple sources.
- Phishing and Scams: Scammers may use your IP footprint to craft convincing phishing emails or messages.
Protecting your IP footprint requires a combination of technical measures and best practices. Using firewalls, antivirus software, and secure connections can help safeguard your data from unauthorized access.
How to Minimize Your IP Footprint
Minimizing your IP footprint is an effective way to protect your privacy and enhance your security. Here are some strategies to consider:
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet traffic and masks your IP address, making it harder for third parties to track your activity.
- Enable Private Browsing: Most browsers offer private browsing modes that prevent your IP address from being logged by websites.
- Adjust Privacy Settings: Review the privacy settings on your devices and apps to limit data collection.
- Use Tor: The Tor network anonymizes your internet traffic by routing it through multiple servers, effectively hiding your IP address.
Implementing these measures can significantly reduce the size and impact of your IP footprint. However, it's important to note that no method is foolproof, and a layered approach to security is often the most effective.
Tools to Track and Analyze IP Footprints
Several tools are available to help you track and analyze your IP footprint. These tools can provide valuable insights into how your data is being collected and used:
- IP Lookup Services: Websites like WhatIsMyIPAddress.com allow you to check your current IP address and view associated geolocation data.
- Network Monitoring Tools: Tools like Wireshark enable you to monitor your network traffic and identify potential vulnerabilities.
- Privacy Audits: Conducting a privacy audit can help you assess the extent of your IP footprint and identify areas for improvement.
Using these tools responsibly can help you stay informed about your digital presence and take proactive steps to protect your privacy.
Legal and Ethical Considerations
The use of IP footprints raises important legal and ethical questions. Here are some key considerations:
- Data Protection Laws: Regulations like the General Data Protection Regulation (GDPR) impose strict requirements on how IP addresses and other personal data can be collected and used.
- Consent and Transparency: Websites and services must obtain user consent before collecting and processing IP data. Transparency about data usage is also essential.
- Surveillance and Monitoring: The use of IP footprints for surveillance purposes raises ethical concerns about privacy and civil liberties.
Understanding these considerations can help you navigate the complex landscape of online privacy and ensure compliance with relevant laws and regulations.
Real-World Applications of IP Footprints
IP footprints have a wide range of real-world applications, both positive and negative. Here are some examples:
- Targeted Advertising: Advertisers use IP footprints to deliver personalized ads based on user behavior and preferences.
- Law Enforcement: IP footprints can be used to trace the origin of illegal activities and identify suspects.
- Content Personalization: Streaming services and websites use IP data to tailor content recommendations to individual users.
While these applications offer benefits, they also highlight the need for responsible data management and user consent.
Conclusion
In conclusion, IP footprints are an integral part of our online interactions, shaping how we connect, communicate, and consume content on the internet. While they enable essential functions like website access and data transfer, they also pose significant challenges to privacy and security. By understanding how IP footprints are created and managed, you can take proactive steps to protect your digital presence.
We encourage you to implement the strategies outlined in this article to minimize your IP footprint and safeguard your online activity. Whether you choose to use a VPN, adjust your privacy settings, or conduct regular audits, every step counts toward a more secure and private internet experience. If you found this guide helpful, please consider sharing it with others or leaving a comment below. For more insights on digital privacy and security, explore our other articles on related topics.
Best Rooftop Restaurants In Chicago: A Complete Guide To Elevated Dining
How Much Does It Cost To Visit Westminster Abbey: A Comprehensive Guide
TodayTix: The Ultimate Guide To Booking Broadway And Theater Tickets

What is Digital Footprinting in Cybersecurity? sunnyvalley.io
What is a Digital Footprint and How to Protect it? SecurityHQ